Computers are used by everyone
People intent on stealing your data or depriving you of it are committing criminal offences. The good news is, that if they used a computer or other digital device as a tool to carry out their deeds, then they will have left tracks that we can find.
We have carried out many hundreds of computer examinations and we never cease to be amazed at the lengths people will go to when stealing, deleting, modifying or accessing data they have no legitimate right to.
The few case types below highlight some of the more common work we have carried out.
HR Investigations
The inappropriate use of company computer or mobile telephone resources, the sending of harassing or pornographic material by email or the accessing of sensitive personal data - just a few of the many ways that digital devices become central to a formal investigation by the Human Resources department.
It's vital in such cases that specialists are employed who can capture the data so that it can be relied upon at a later date. Many clear cut cases fail because a manager decided that it would be helpful for someone from IT to have a quick look to substantiate the allegation. IT staff are not trained for this and will change the data, simply be looking at it, the last access dates and times will have been altered - irrevocably.
We are experienced at ensuring all of the aspects of the investigation are carried out correctly. From covert data acquisition, data analysis and reporting. We provide clear, easy to follow forensic reports which present the facts in plain English, providing expert opinion where this is appropriate. We can assist with interviewing the subject and if necessary will provide evidence at an internal HR hearing, or at an industrial tribunal. Our processes are designed to withstand the scrutiny that comes from giving evidence at court. This same level of diligence is carried out on all our casework be default.
Intellectual Property Theft
Data theft always leaves a trace of some sort. Modern computer systems are too complex for even a knowledgeable user to completely eradicate their steps. modern operating systems maintain encrypted caches of user activity logs, secreted away in system-only databases or in backup areas that most users aren't even aware exist.
Whenever a USB device is plugged in to a Windows computer, for example, unique encoded entries are written into the computers Registry which record the fact. We know where to find and decode them.
We have helped many companies investigate data theft, not just of company documents from employees attempting to create a competing start-up, but sensitive customer databases and extremely valuable intellectual property, including designs and patents.
As a result of our analysis of email and server data, the evidence we produce has been used to obtain civil search orders from the court, to compel an employee to allow an examination of their computer equipment for copies of the data in question. We have helped companies recover their data and obtain court orders preventing the thieves from contacting their employers customers.
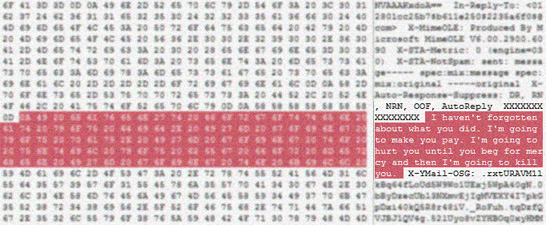
Fraud and Forgery
With the emergence of desktop publishing and the ability to create high quality documents, fraudsters have enjoyed unparalleled success in their ventures. Often, it takes a trained document expert to differentiate the fake from the real thing once printed out.
Helpfully, this task is easier when examining the artefacts left behind by the fraudster. The tell-tales include the presence of high-end professional graphics and desktop publishing applications, folders of graphics files and scans or photographs of original documents.
Whilst these artefacts are reasonably straightforward to find, there are subtleties which only a trained analyst experienced in this field will locate and put into the correct context.
Often with fraud, it's the time line which is the most significant factor. People who produce documentary evidence after the fact about an event from which they stand to lose or gain a great deal. Nothing short of a highly trained and experienced specialist in computer based dates and times will make sense of the myriad of data that surrounds such an enquiry. We have the skills and experience to put the pieces in the correct order and to provide a compelling narrative of the fraudsters activities.
What to do next?
If you'd like to know more about how we can help with your particular situation, give us a call for free confidential advice, or drop us an email and we'll get straight back to you.



